Cloud Data
Protection Platform
Put your business on the fast track to success without changing the existing data environment.

If you leave any further inquiries, we will contact you after checking. Inquiries regarding a demo request can be made within the Request a demo page.
Why QueryPie?
Features optimized for cloud environments can help you build a more secure security system.

Automated Discovery
Automatically find, identify and secure sensitive data across distributed databases & applications

Cloud Centric
Auto-tracking the lifecycle of data sources in the cloud and detect security threats via cloud API integrations.

Integrated IAM & SIEM
Increase data accessibility and security. and decease the data breach possibilities via IAM and SIEM
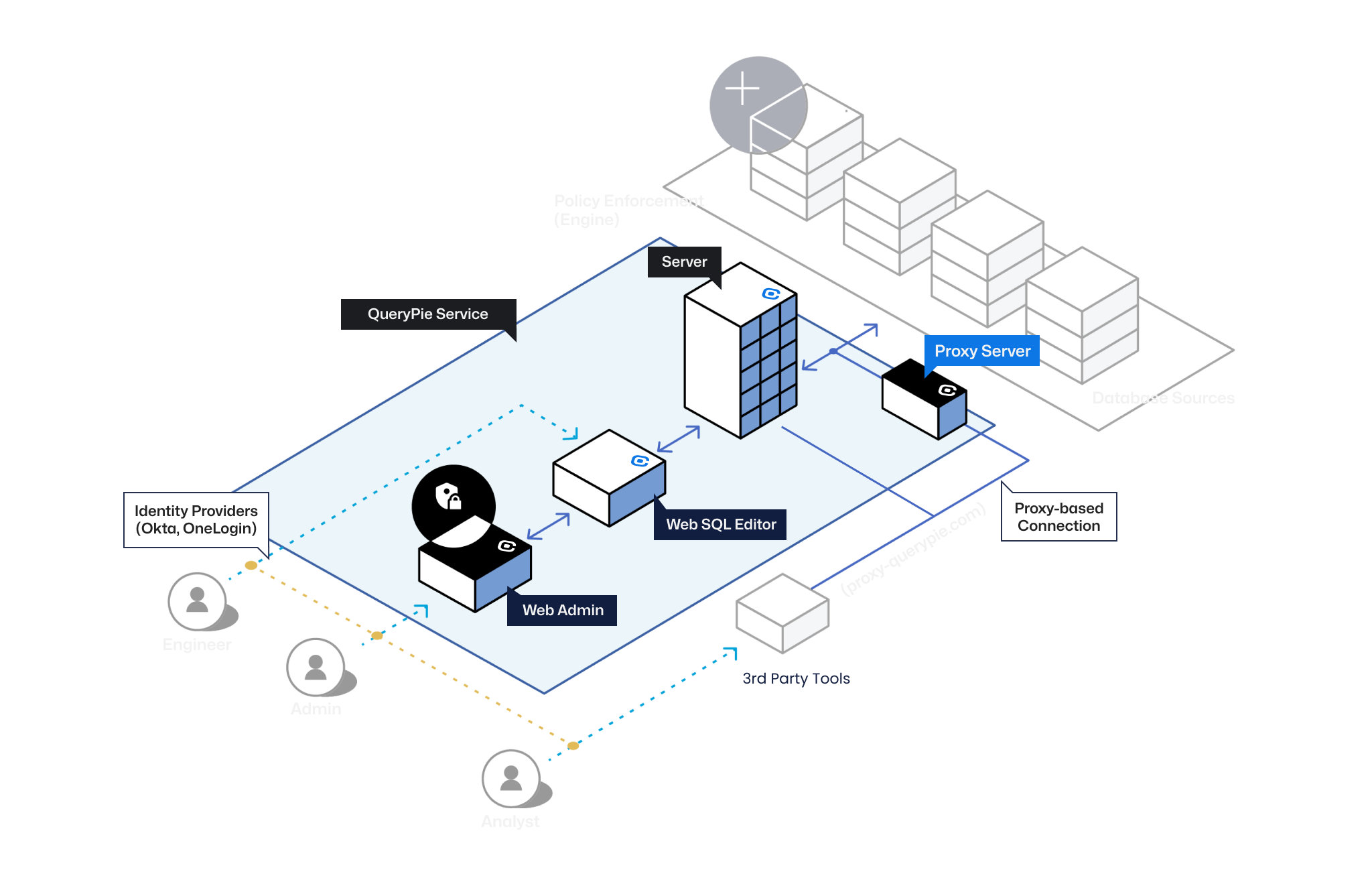
QueryPie Solutions
Effortlessly manage and safeguard access to your databases and systems with QueryPie,
ensuring only authorized users have the privilege to query sensitive data. Rest easy knowing that QueryPie also ensures compliance with industry regulations, helping you meet data privacy and security standards with confidence.
Platform Integrations

Get Started today!
Let us show you how QueryPie can transform the way you govern and share your sensitive data.


